# rhabdomancer
[](https://github.com/0xdea/rhabdomancer)
[](https://crates.io/crates/rhabdomancer)
[](https://crates.io/crates/rhabdomancer)
[](https://twitter.com/0xdea)
[](https://infosec.exchange/@raptor)
[](https://github.com/0xdea/rhabdomancer/actions/workflows/build.yml)
[](https://github.com/0xdea/rhabdomancer/actions/workflows/doc.yml)
> "The road to exploitable bugs is paved with unexploitable bugs."
>
> -- Mark Dowd
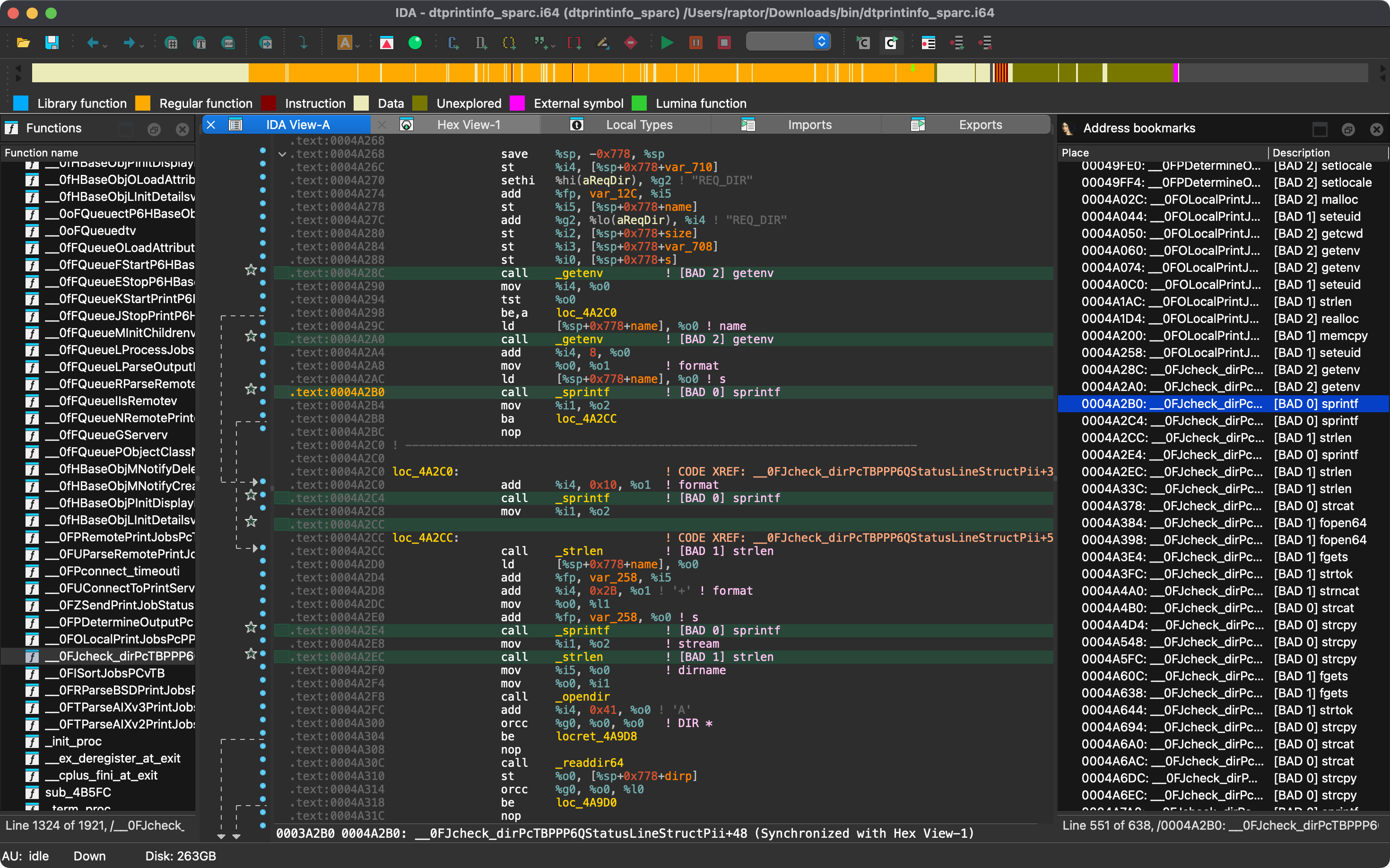
Rhabdomancer is a blazing fast IDA Pro headless plugin that locates all calls to potentially insecure API functions in
a binary file. Auditors can backtrace from these candidate points to find pathways allowing access from untrusted input.
## Features
* Blazing fast, headless user experience courtesy of IDA Pro 9 and Binarly's idalib Rust bindings.
* Support for C/C++ binary targets compiled for any architecture implemented by IDA Pro.
* Bad API function call locations are printed to stdout and marked in the IDB.
* Known bad API functions are grouped in tiers of badness to help prioritize the audit work.
* [BAD 0] High priority - Functions that are generally considered insecure
* [BAD 1] Medium priority - Interesting functions that should be checked for insecure use cases.
* [BAD 2] Low priority - Code paths involving these functions should be carefully checked.
* The list of known bad API functions can be easily customized by editing `conf/rhabdomancer.toml`.
## Blog post
* <https://security.humanativaspa.it/doing-vulnerability-research-with-ida-pro-and-rust> (*coming soon*)
## See also
* <https://github.com/0xdea/ghidra-scripts/blob/main/Rhabdomancer.java>
* <https://docs.hex-rays.com/release-notes/9_0#headless-processing-with-idalib>
* <https://github.com/binarly-io/idalib>
* <https://books.google.it/books/about/The_Art_of_Software_Security_Assessment.html>
## Installing
The easiest way to get the latest release is via [crates.io](https://crates.io/crates/rhabdomancer):
1. Download, install, and configure IDA Pro (see <https://hex-rays.com/ida-pro>).
2. Download and extract the IDA SDK (see <https://docs.hex-rays.com/developer-guide>).
3. Install rhabdomancer as follows:
```sh
$ export IDASDKDIR=/path/to/idasdk90
$ export IDADIR=/path/to/ida $ cargo install rhabdomancer
```
## Compiling
Alternatively, you can build from [source](https://github.com/0xdea/rhabdomancer):
1. Download, install, and configure IDA Pro (see <https://hex-rays.com/ida-pro>).
2. Download and extract the IDA SDK (see <https://docs.hex-rays.com/developer-guide>).
3. Compile rhabdomancer as follows:
```sh
$ git clone https://github.com/0xdea/rhabdomancer
$ cd rhabdomancer
$ export IDASDKDIR=/path/to/idasdk90 $ export IDADIR=/path/to/ida $ cargo build --release
```
## Usage
1. Make sure IDA Pro is properly configured with a valid license.
2. Customize the list of known bad API functions in `conf/rhabdomancer.toml` if needed.
3. Run rhabdomancer as follows:
```sh
$ rhabdomancer <binary_file>
```
Any existing `.i64` IDB file will be updated; otherwise, a new file will be created.
4. Open the resulting `.i64` IDB file with IDA Pro.
5. Select `View` > `Open subviews` > `Bookmarks`
6. Enjoy your results conveniently collected in an IDA Pro window.
*Note: rhabdomancer also adds comments at marked call locations.*
## Tested with
* IDA Pro 9.0.240925 on macOS arm64 and Linux x64.
* IDA Pro 9.0.241217 on macOS arm64 and Linux x64.
*Note: not tested on Windows, check [idalib](https://github.com/binarly-io/idalib) documentation if you want to try it
yourself.*
## Changelog
* [CHANGELOG.md](CHANGELOG.md)
## TODO
* Enrich the known bad API function list (see <https://github.com/0xdea/semgrep-rules>).
* Implement a basic ruleset in the style of [VulFi](https://github.com/Accenture/VulFi)
and [VulnFanatic](https://github.com/Martyx00/VulnFanatic).